Under Attack: Hackers Find Construction Data Attractive Target
Article written by Steven H. Miller and appears on Constructor Magazine.com.

There is an old adage concerning timely action about the uselessness of locking the stable after the horse is gone. It is, unfortunately, the story of many construction companies confronting the issue of cybersecurity. They never considered themselves a target until it was too late.
Many are surprised by how fast the future has arrived, but it is here now. From payroll and tool-tracking to 3D building models and as-built laser scans, a construction company’s network is the conduit for increasing portions of its activities and is hosting an increasing number of outsiders and their devices. That is an attractive target for thieves, especially since the number of vulnerabilities in the network is growing. If the ‘stable’ in the old adage is your computer network with 250 doors instead of one and strangers going in and out, locking it up is not a simple task. To avoid becoming a victim, cybersecurity must be considered a top issue.

 Submittals are one of the most vital parts of the processes and workflows around construction projects. The submittal process assures owners that their plans and specs are clearly understood by both contractors and subcontractors building the project. This process ensures both quality control and contractual compliance per the plans and specifications.
Submittals are one of the most vital parts of the processes and workflows around construction projects. The submittal process assures owners that their plans and specs are clearly understood by both contractors and subcontractors building the project. This process ensures both quality control and contractual compliance per the plans and specifications.
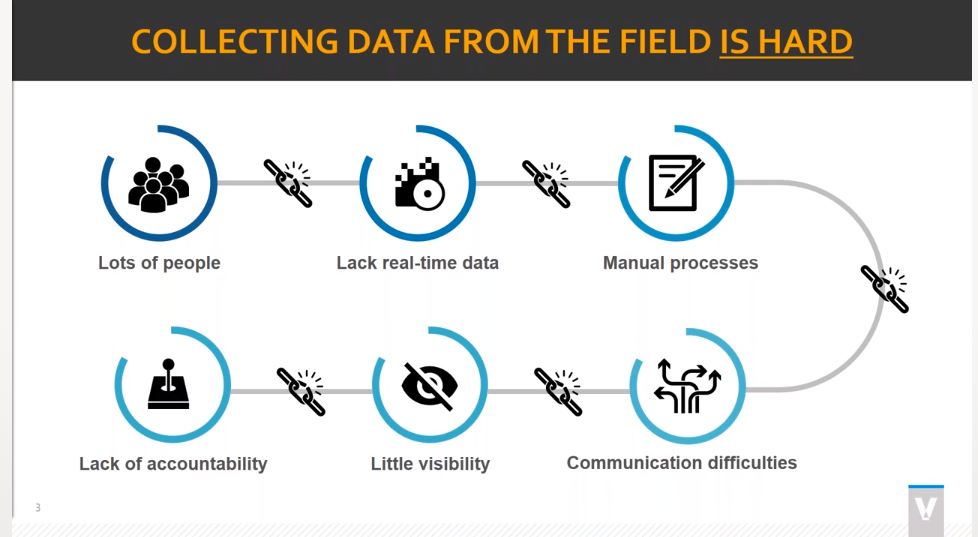
 Construction projects today produce a mountain of data. From job costs to materials quantities to equipment usage to labor and production stats, data drives how successful a project will be. The most successful projects — and contractors — are able to accurately collect all available data and analytically dig deep into it to better understand projects. But that’s easier said than done.
Construction projects today produce a mountain of data. From job costs to materials quantities to equipment usage to labor and production stats, data drives how successful a project will be. The most successful projects — and contractors — are able to accurately collect all available data and analytically dig deep into it to better understand projects. But that’s easier said than done.